A Case Study in Crypto Asset Recovery

This post-mortem case study documents Resolv’s investigation into the theft of 1,010 pUSDC (approximately $1,010 USD). The user approved a malicious smart contract, inadvertently granting permissions that allowed their funds to be extracted and transferred through multiple wallets to obscure the trail. Following a thorough investigation, Resolv’s jurors validated the user’s claim and recommended full restitution of the funds. Resolv proceeded to return the assets to their rightful owner.
Incident Details
-
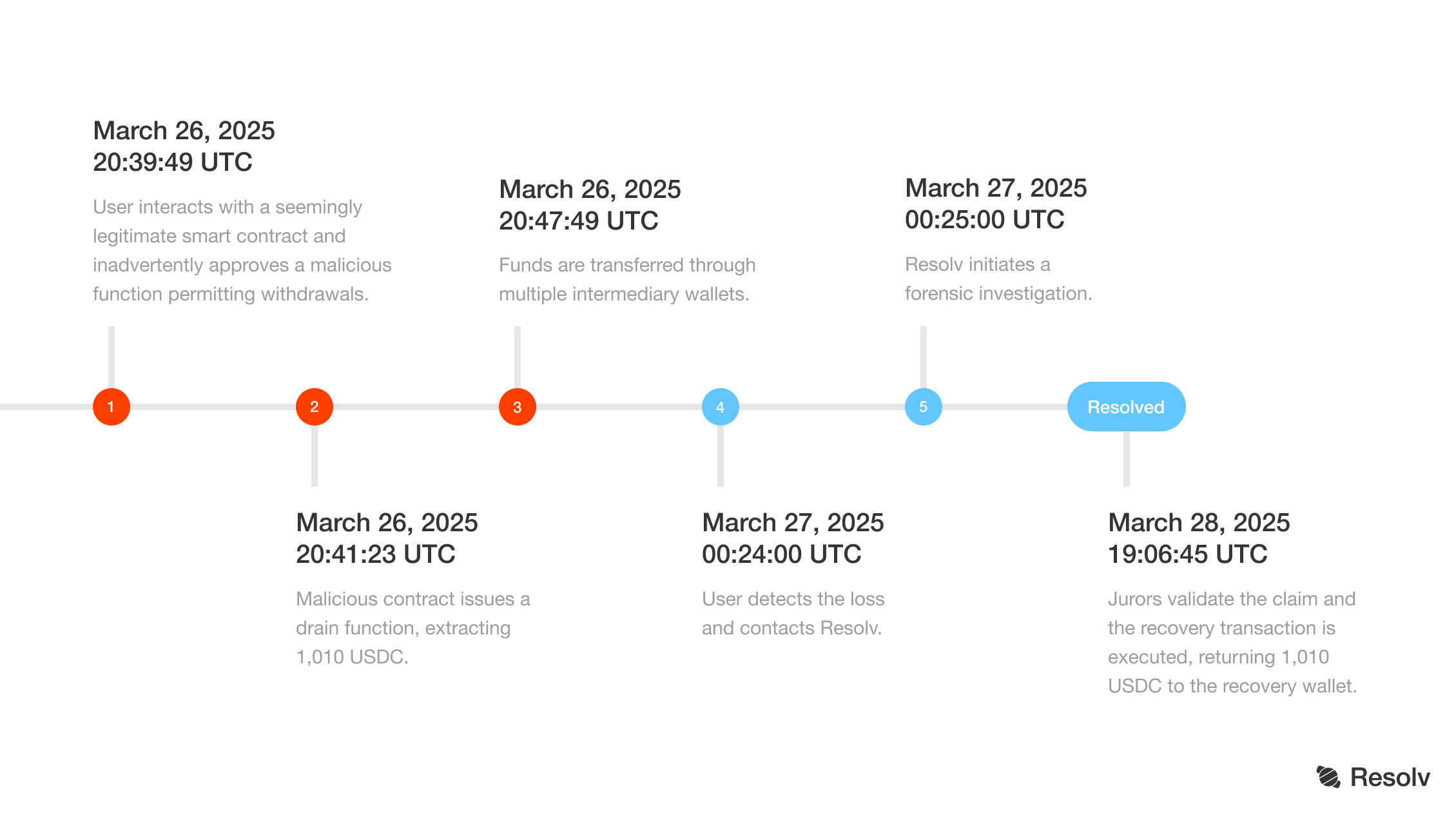
Attack date: March 26, 2025
-
Victim’s wallet: 0x92F9E69333A78829382687A856D2AF66Ff3fbE36
-
Malicious contract: 0x15294dcACc612051D42F6b9DF941084c3f5B1154
-
Assets stolen:1,010 pUSDC ($1,010 USD)
-
Theft transaction hash
Attack Timeline
Investigation Methodology
1. Smart Contract Analysis
Resolv’s jurors decompiled and analyzed the bytecode of the malicious contract, identifying the following critical functionalities:
a. Ownership and Control
-
The contract has an owner() function consistent with the Ownable pattern, meaning someone has special control over it. This is a common setup in many contracts.
-
Another storage slot holds a token or target address, likely used to either take tokens or send them elsewhere (used for draining and forwarding).
b. Drain Functions
-
Token Grabber (Function Code: 0xbfa2c1d2): This part of the code allows the owner to move ERC20 tokens from any wallet that gave the contract permission. It’s like having a key to someone else’s account.
-
Mass Theft (Function Code: 0x0e0d3a9c): This is a batch-drain function which loops through multiple [from] addresses and [amounts] to perform [transferFrom] calls, meaning it can steal tokens from many wallets at once. It automates the process of draining multiple accounts.
c. ETH Fallback Behaviour
-
A receive() function automatically forwards any received ETH to a pre-set address.
-
This indicates an intent to automatically funnel assets elsewhere upon receipt: the contract was designed to grab any funds it could, and pass them through for immediate laundering.
d. Inferred Purpose
-
The contract’s architecture is purpose-built to extract ERC20 tokens from victims upon approval, clearly designed for unauthorized token theft
-
The owner is the only address authorized to invoke these draining functions.
-
In short, the contract is built for one purpose: to steal tokens from users who unknowingly give it permission.
2. On-Chain Transaction Tracing
We mapped the flow of funds:
a. Initial Drain
-
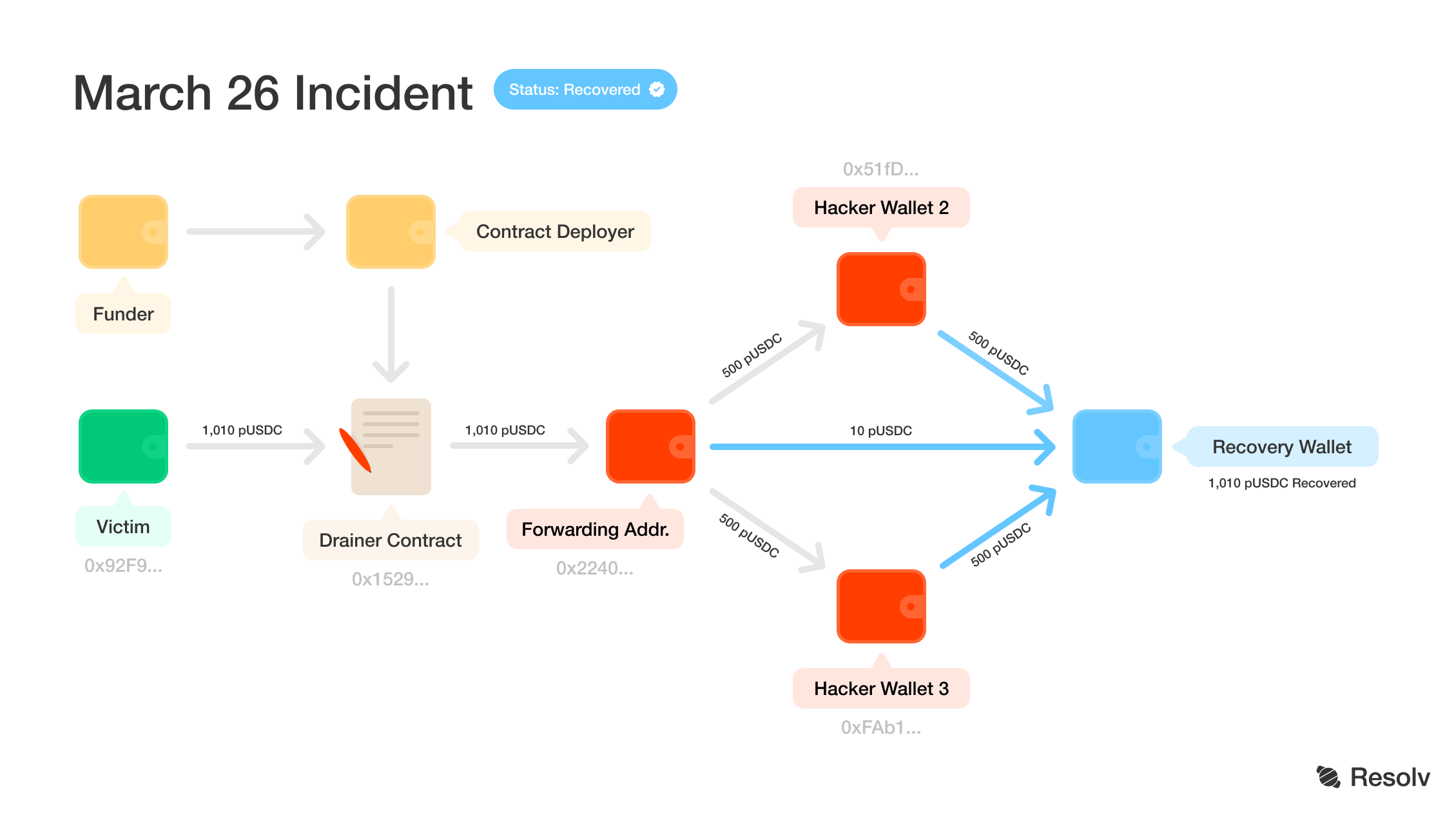
The initial flow of funds began from the user’s wallet (0x92F9E69333A78829382687A856D2AF66Ff3fbE36) to the intermediary wallet (0x2240b0DB8c4aAffaf482EE87bCFFb5B41759312b). This transaction involved an amount of 1,010 pUSDC.
-
The transaction hash
3. Multi-Hop Transfers
The funds in the intermediary wallet (0x2240b0DB8c4aAffaf482EE87bCFFb5B41759312b) were fragmented into two separate transfers to other addresses:
a. First Transfer:
-
Destination address: 0x51fD6Ca46bdf720b2618993442c1900e588625FA
-
Amount:500 pUSDC
-
Transaction hash
b. Second Transfer:
-
Destination address: 0xFAb1a45F6a2A32A30370d2dF2215E36293772038
-
Amount:500 pUSDC
-
Transaction hash
c. Recovery
After reporting the incident, the stolen pUSDC were first frozen then returned to the user’s recovery wallet 0x26d96d924c43eb9690f789454bdfff80085d725e. This is possible because freeze and recovery functions are built directly into the pUSDC token contract — allowing Resolv to automatically retrieve assets once fraud is confirmed.
Evidence of Malicious Activity
Several indicators support the conclusion that the user’s funds were removed without authorization, based on analysis of the transaction data, contract code, and user testimony:
-
Suspicious Timing:The approval of the drainer contract and the subsequent removal of funds occurred in immediate succession, with no legitimate service or exchange involved. This rapid sequence suggests a direct exploit of the user’s approval.
-
Lack of User Consent:There is no indication that the user expected their funds to be moved or that they engaged in any service that would warrant such a transfer. The user reports that they mistakenly approved the drainer contract, further supporting the conclusion of unauthorized fund removal.
-
Multi-hop Transfers:The funds were rapidly transferred through several additional wallets after leaving the user’s account. These “multi-hop” transfers are a known laundering strategy used to obscure fund flow, making it more difficult to trace the stolen assets.
-
Malicious Contract Design:The contract’s structure and function signatures (e.g., drain, drainBatch) explicitly suggest malicious use for token draining once approval is granted. The contract was designed to facilitate non-consensual token transfers.
Jurors’ Assessment and Recommendations
After reviewing the evidence, Resolv’s jurors [comprised of a decentralized group of on-chain forensic investigators] determined:
-
Claim validation: Analysis confirms that funds were extracted through a malicious contract without the user’s informed consent.
-
Restitution recommendation:Full return of the 1,010 pUSDC to the affected user is recommended.
-
Additional preventive measures:
-
Adding contract 0x15294dcACc612051D42F6b9DF941084c3f5B1154 to the protocol’s blacklist
-
Updating detection mechanisms to identify similar attack patterns
Lessons Learned and Best Practices
This case highlights the importance of:
-
Approval management: Using tools like revoke.cash to regularly audit and revoke unnecessary permissions.
-
Response speed: Swift detection and reporting of incidents significantly increases the chances of recovery.
-
Contract verification: Always verify the legitimacy of contracts before granting approvals:
-
Check source code on Etherscan or other blockchain explorers
-
Verify the reputation and age of the contract
-
Limit approval amounts when possible
4.Continuous education:Stay informed about the latest attack techniques in the DeFi ecosystem.
Conclusion
This case highlights the risks that can come with using smart contracts, especially ones that haven’t been properly verified. In this instance, a known exploit was used to take 1,010 pUSDC from a user’s wallet without permission. A closer look at the code confirmed the attack followed a familiar pattern. Thankfully, Resolv’s arbitration process kicked in and worked as intended. The stolen funds were recovered and returned to the user, showing how effective Resolv’s tools can be in handling and resolving these kinds of situations.
This case study was prepared by the Resolv team. For more information about our asset recovery services or to report an incident, visitresolv.financeor contact our team at admin@resolv.finance